Most of the Cloudian guides suggest using HA-Proxy or similar as a Load Balancer in front of the Cloudian nodes.
However, If you have an Existing Fortigate we can use that. I want to:
- Use the Fortigate to distribute S3 traffic to all nodes in the cluster.
- Provide SSL offload so we have an easy place to manage and update certificates
- Still have HyperIQ and Cloudian report correct Client IP addresses
Fortunately, that’s all pretty easy with the Fortigates.
Upload your certificate. For publicly accessible S3 you will need a multi SAN wildcard cert. Also with the variety of tools available to connect (AWS CLI, GO tools) etc. getting a well supported cert is important. If your FQN for Cloudian system is example.com, then you will need to cover the following:
- *.example.com (The ‘normal’ wildcard domain, [covers, cmc, iam and top level s3 access])
- *.s3-region1.example.com (covers region1 buckets)
- *.s3-website-region1.example.com (covers region1static web content)
If you have multiple regions then you will need to add those too. For CA we chose Digicert Thawte Multi-SAN wildcard and that seems to work fine with aws cli tools. Upload the local cert as PKCS#12 format.
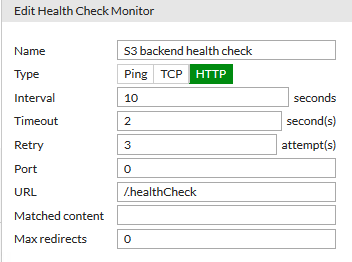
Create health check rule. Optional step, but we can’t just monitor http content here. Cloudian provides a .healthCheck url which returns a 200 http response with 0 length content. Don’t forget the leading /
Create Virtual Server (FGT speak for Load Balancer)
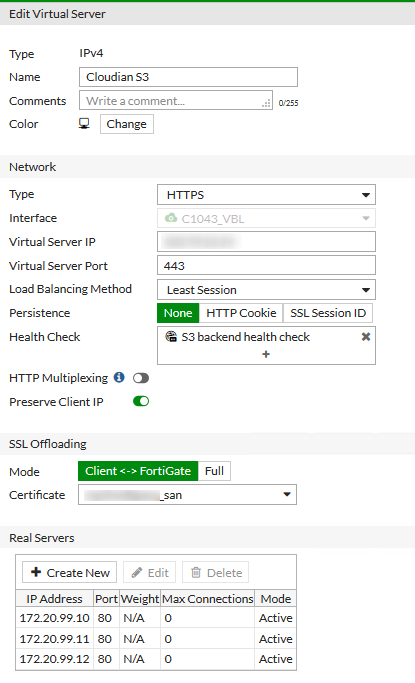
Set Preserve Client IP. This sets the X-Forwarded-For header.
Benchmarking doesn’t show a huge difference between the Load Balancing methods, and since S3 requests are stateless, we don’t need Static (you need Static is you want to hide your CMC or API admin ports being a load balancer) . I felt that ‘Least Session’ was enough to try and distribute the requests to all working nodes.
SSL Offloading manages the Client to Load Balancer encrypted sessions. But we don’t need to re-encrypt to talk to the Cloudian nodes on the backend. This means that Cloudian itself only needs to be configured for S3 on port 80, which makes life a lot simpler.
Check Load Balancer monitor to see all backend nodes are up.

Configure Cloudian to report/honor the X-Forwarded-For heading (else all you client IP addresses will be reported as the inside address of the load balancer
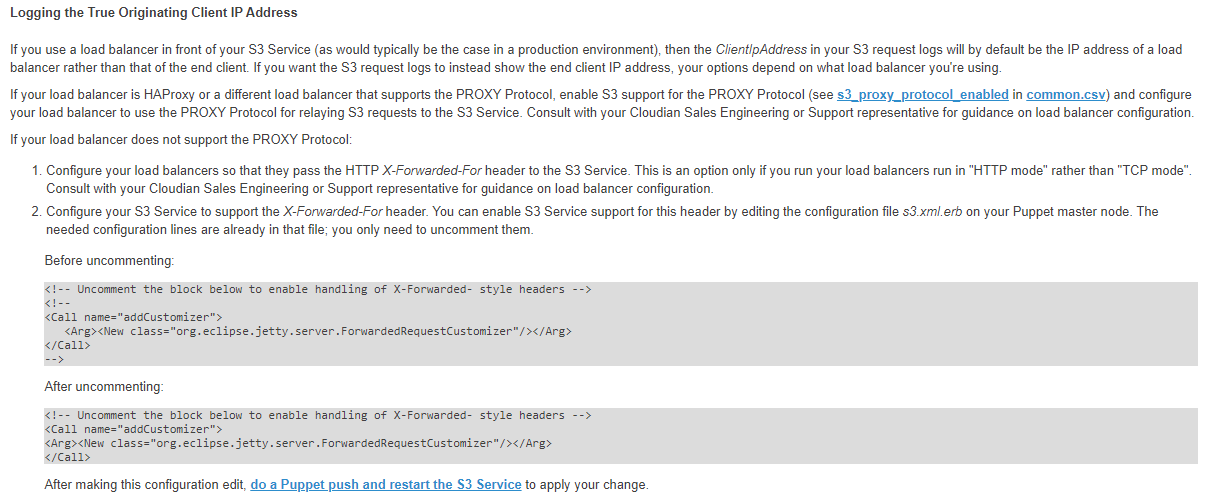
Now, the FGT is not using the PROXY protocol, we need to configure the section for handling the right headers. Ans also if you have configured Object Lock, then you will need to condifgure this through the avaialble cli tools
sa_admin@s3chchs01$ hspkg config --edit s3.xml.erb
Uncomment the block to enable handling of X-Forwarded- style headers
Run hspkg install and 2 (Cluster Management) b ( Push Configuration Settings to Cluster)
The restart S3. (Run hspkg install and 2 (Cluster Management) c (Manage Services) 5 (S3 service) restart)
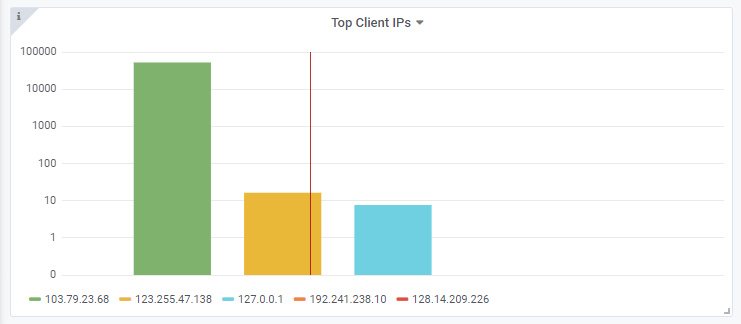
If you are using HyperIQ (with Enterprise license for S3 insights) then that will now display the correct client IP addresses