So, we had some “new” APC PDU installed in a rack. Normally these should just grab DHCP address and we’re off. But in this case I had 2 that simply were not playing ball.
Looking at the attached switch ports, could see that the devices were up, and we could see and appropriate MAC address on each interface.
SW2> show ethernet-switching table interface ge-0/0/34
MAC database for interface ge-0/0/34
MAC database for interface ge-0/0/34.0
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static, C - Control MAC
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC)
Ethernet switching table : 1 entries, 1 learned
Routing instance : default-switch
Vlan MAC MAC Age Logical NH RTR
name address flags interface Index ID
Test VLAN 28:29:86:53:3b:85 D - ge-0/0/34.0 0 0
{master:0}
SW2> show ethernet-switching table interface ge-0/0/35
MAC database for interface ge-0/0/35
MAC database for interface ge-0/0/35.0
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static, C - Control MAC
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC)
Ethernet switching table : 1 entries, 1 learned
Routing instance : default-switch
Vlan MAC MAC Age Logical NH RTR
name address flags interface Index ID
Test VLAN 28:29:86:53:2e:86 D - ge-0/0/35.0 0 0
{master:0}
I can see from the DHCP monitor, that nothing is being assigned
Lets try and find out what the device thinks it is. If it’s alive it shoudl be sending out some sort of arp traffic or IPv6 neighbour solicitaion messages….
The Fortgate diagnose sniffer command is pretty powerful, but how do you filter for specific mas addresses.
Well to find 28:29:86:53:3b:85 and the source we use:
diagnose sniffer packet any "(ether[6:4]=0x28298653) and (ether[10:2]=0x3b85)" 4This is taken from this KB article, but I wondered why the 6 byte length is split into a 4 and 2. Why not just match 6 bytes at once? Turns our you can only match on 1,2 or 4 byte with the pcap filters.
diagnose sniffer packet any "(ether[6:6]=0x282986533b85)" 4
interfaces=[any]
filters=[(ether[6:6]=0x282986533b85)]
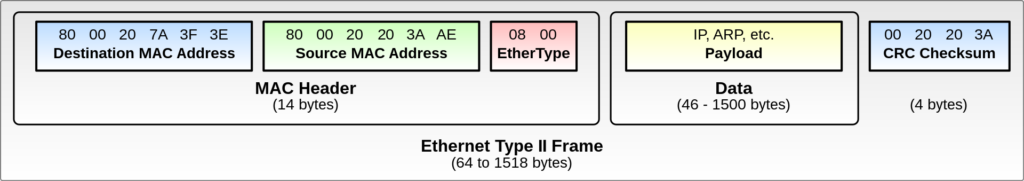
pcap_compile: data size must be 1, 2, or 4The first 6 bytes of an Ethernet frame are th Destination MAC address and the second 6 are the Source MAC address.
Bounce the switch port and when I look at the output, we can see the ARP requests coming from the device and the IP address it has been confirgured with.
FW2 (Internal) # diagnose sniffer packet any "(ether[6:4]=0x28298653)" 4
interfaces=[any]
filters=[(ether[6:4]=0x28298653)]
44.401628 port4 in 802.1Q vlan#1234 P0
44.401630 ae0 in 802.1Q vlan#1234 P0
44.401631 INT_1 in fe80::2a29:86ff:fe53:2e86.546 -> ff02::1:2.547: udp 56 [hlim 1]
44.401656 port6 in 802.1Q vlan#1234 P0
44.401657 ae1 in 802.1Q vlan#1234 P0
44.401657 INT_1 in fe80::2a29:86ff:fe53:2e86.546 -> ff02::1:2.547: udp 56 [hlim 1]
76.194772 port4 in 802.1Q vlan#1234 P0
76.194774 ae0 in 802.1Q vlan#1234 P0
76.194774 INT_1 in arp who-has 10.26.168.97 tell 10.26.168.104
76.194779 port6 in 802.1Q vlan#1234 P0
76.194780 ae1 in 802.1Q vlan#1234 P0
76.194780 INT_1 in arp who-has 10.26.168.97 tell 10.26.168.104ports/interfaces/vlans have been changed to protect the innocent… But you can see the device has the statically configured IP 10.26.168.97. Accessing it is another matter….
